 Dealing with malware on Macs has been a non-issue until recent weeks. The “Mac Defender” trojan seems to have affected many Mac users, particularly the ones active on the web. Thankfully this is a weak trojan horse that is difficult to get, easy to remove and doesn’t cause any real damage. Most importantly, it does not try to spread itself like a virus.
Dealing with malware on Macs has been a non-issue until recent weeks. The “Mac Defender” trojan seems to have affected many Mac users, particularly the ones active on the web. Thankfully this is a weak trojan horse that is difficult to get, easy to remove and doesn’t cause any real damage. Most importantly, it does not try to spread itself like a virus.
MacMost has launched a new section, the Mac Virus and Malware Information Center. Here we have posted information and a video about the Mac Defender trojan. You can find out how to avoid it and how to remove it. In the future, we can update that section and post information there about other malware that may spring up.
Sometimes an app idea can seem ridiculous, but after trying it, you feel compelled to use it again later. Then again. Then the next thing you know it is one of your top apps. Foursquare is a location game. You “check in” at a restaurant, park, airport or wherever and get points for your check-ins. You link up with friends and compete against them to see who gets around more. You can also share notes, tips and pictures of places with friends and the whole world. It goes without saying that this isn’t for someone concerned about privacy. With the right group of friends, you can have fun and discover new places.
So you know those icons that appear in the upper right part of your screen in the menu bar? If you want to re-arrange them, all you need to do is hold the Option and Command keys down, and then click and drag the icons left or right. You can also remove an icon by dragging it down and out of the menubar.
“Using AirPlay on my iPad I can show you my vacation photos on the big screen! Isn’t technology great?”
“Uh, sure.”
“We have to go…”
Learn about the Mac Defender/Mac Protector trojan horse malware attack. See how it works. Find out how to protect yourself from it. Watch step-by-step how to remove it. This piece of malware tricks you into download and installing it with frightening, but completely fake, virus warnings. What it really wants is your credit card number. Fortunately it is easy to avoid and easy to remove.
Update, August 1, 2011: Apple released a security update (2011-003) on June 1 that catches and removes this trojan for Snow Leopard users. New variants appeared, but Apple updated to counter those versions as well. Lion is not threatened by this malware. So this trojan is only a threat if you have a non-updated version of Snow Leopard or Leopard. However, it seems to have disappeared as a threat.
Check out MacMost Now, episode 555: Mac Defender Trojan for a video tutorial on this problem, how to avoid it, and how to clean your Mac if you have it.
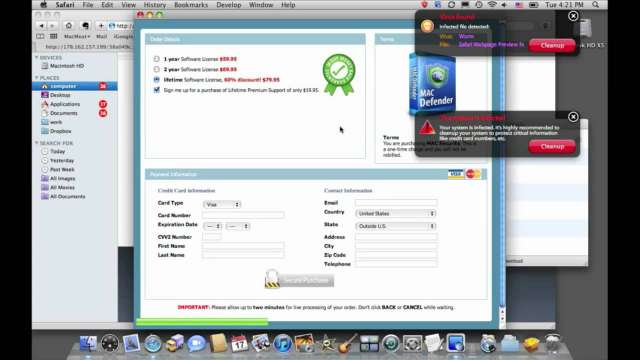
The Mac Defender trojan, also know as the Mac Protector, Mac Security or Mac Guard trojan, is a clever deception that works like this:
- The user searches for something on the web and clicks on a link. Sometimes the bad link is part of a comment left at a news site.
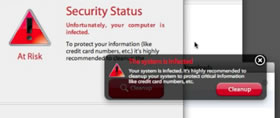
- The page pops up various screens and graphics to make it appear as if the web page has detected a virus on your Mac. It is all fake.
- If you click on anything on that page, including the cancel button, a you will download the malicious “Mac Defender” installer.
- If you have “Open Safe Files After Downloading” then the installer will launch and run.
- At this point the installer asks for the admin password, to get permission to install. The Mac Guard variant doesn’t ask for a password, but still asks for permission to install.
- If the user gives the password, it installs and infects the Mac.
- Fake virus scanning screens appear and declare that the Mac is infected with a virus, a credit card number is requested so that the Mac can be cleaned.
The malware can be easily thwarted at almost any step along the way. Here are ways to protect yourself.
- If you come across a page on the web that says, in any way, that you are infected with a virus, just force-quit Safari. Control+option+click on Safari in the Dock and select “Force Quit,” then confirm the force quit. Do not click any buttons on the page, even if the buttons are labeled “cancel.” A web page cannot analyze your Mac for viruses and those graphics are simply fakes.
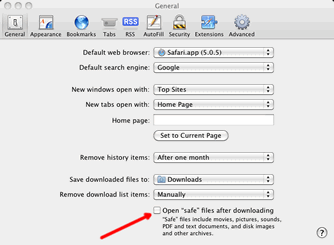 Make sure you set Safari to NOT “Open Safe Files After Downloading.” In Safari, go to Safari, Preferences, General and uncheck it there.
Make sure you set Safari to NOT “Open Safe Files After Downloading.” In Safari, go to Safari, Preferences, General and uncheck it there.- If you have downloaded the file, don’t run it. Delete it from your Downloads folder.
- If the installer has been automatically launched, don’t give it permission to install by entering your admin password. Cancel the install and delete it from your Downloads folder.
- If you have installed it, then you must remove it. Doing so involves a few simple steps:
- Quit the application. Do this by running Activity Monitor. Show all processes in Activity Monitor and look for Mac Defender or Mac Protector. Select and force quit any you find.
- Go to your Applications folder and find the program there. Drag it to the trash and empty trash.
- Check in your System Preferences, Accounts, Login Items for your current account. See if there is any Mac Defender or Mac Protector process listed. If so, remove it.
Notes
Back to the Mac Virus and Malware Information Center.
Many terms are used to describe malware. Some are used to describe the delivery method. Others are used to describe what the malware does.
Delivery Method Terminology
Virus: A computer virus is a piece of malware that makes a copy of itself and attempt to spread itself to other computers over a network. Viruses can infect a computer with little or no action on the user’s part. (Read more: Wikipedia)
Trojan: A trojan is malware application, or an application infected with malware, that the user downloads and installs, not realizing it can cause harm. Like the “trojan horse” it is named after, the software appears to be something else. It does not attempt to spread itself further. (Read more: Wikipedia)
Functionality Terminology
The worst malware attempts to either harm your computer, deleting data, or it tries to steal come critical information like banking numbers or account passwords. Many malware terms apply to what the malware does once it is installed.
Spyware: This would record what you are doing, such as web sites you are visiting or email you receive and report it back to a source. A keylogger is spyware that records each keystroke, perhaps obtaining passwords in the process. Often spyware is installed by the owner of the computer to spy on a user, such as an employee, parent, spouse or school authority. (Read more: Wikipedia)
Adware: This could describe any software that includes advertisements, including completely legitimate software. But sometimes viruses or trojans can show advertisements or replace web advertisements without even implied permission from the user. (Read more: Wikipedia)
Back to the Mac Virus and Malware Information Center.